SUMMARY
ATMs are a lot more vulnerable than we think
Once the malware is installed into the ATM using the ATM Malware card, all the debit card information of customers can be captured
The malware Ploutus-D has been used in recent ATM attacks
Want to hear something both interesting and spine-chilling? An extensive research report published last year reveals that most ATMs can be hacked in 20 minutes or less. Even scarier, 85% of the ATMs tested for the research allowed an attacker access to the network and another 58% had vulnerabilities in their network components or services that could be exploited in order to control the ATM from a remote location.
All of this simply means that ATMs are a lot more vulnerable than we thought. Considering that they not only hold huge amounts of cash but also contain valuable user data, this can be quite a scary thought. Especially since most of us are unaware of how vulnerable to attack ATMs really are.
At CloudSek, we scoured the Dark Web to see what information is available around the different ATM hack strategies. We found rich, diverse information on the different strategies and have tried to encapsulate the basics in this article, in the hope that it helps readers become more aware of what’s out there and how they should stay safe.
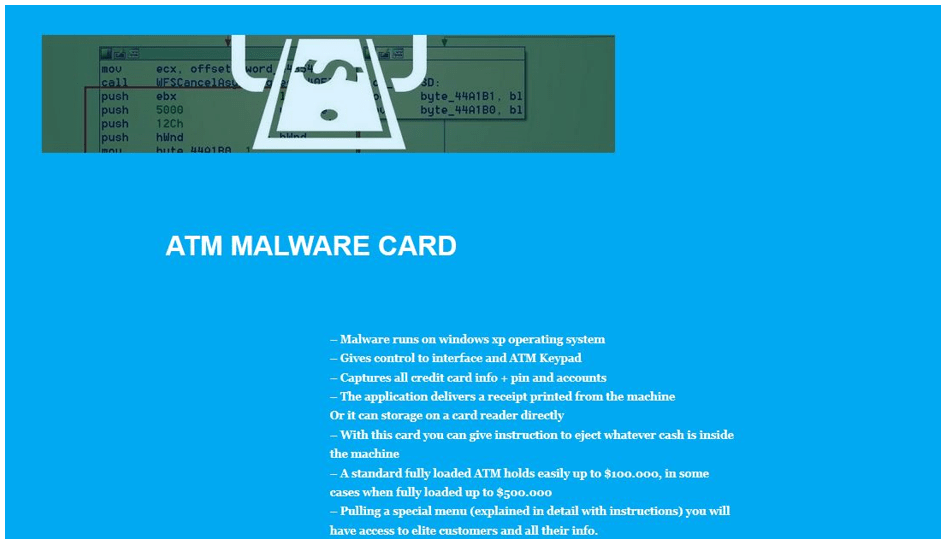
Method 1: ATM Malware Card
This is probably one of the most popular methods that ATM hackers use to exploit vulnerabilities. There are sites on the dark web that deliver an entire malware kit to the customer which includes the ATM Malware Card, PIN Descriptor, Trigger Card and an Instruction Guide.
Once the malware is installed into the ATM using the ATM Malware card, all the debit card information of customers can be captured from the machine. Hackers then use the Trigger Card to dispense the cash from the ATM. All in all, this is one of the most popular methods on the dark web and comes with fairly detailed, step-by-step instructions on how to execute. This method is supported by the machines that are running Windows XP.
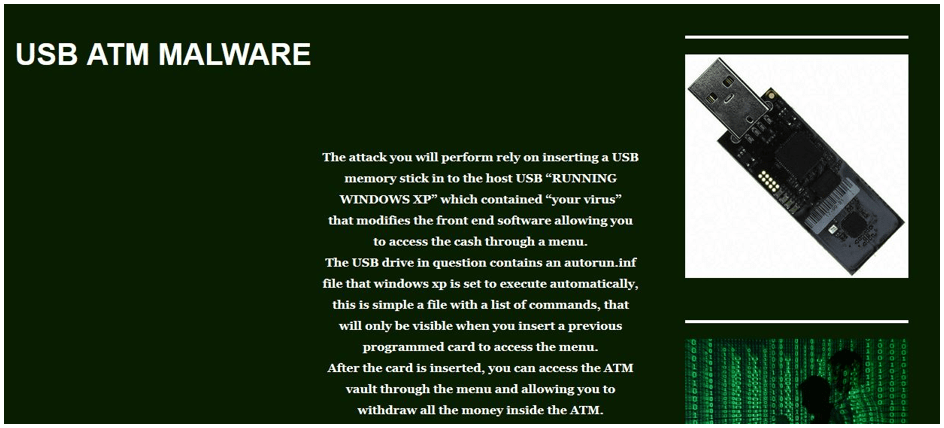
Method 2: USB ATM Malware
This is another prevalent method for machines that support Windows XP. It enables hackers to dispense all the cash from the ATM machine by using the Malware-hosted USB drive to infect the machine.
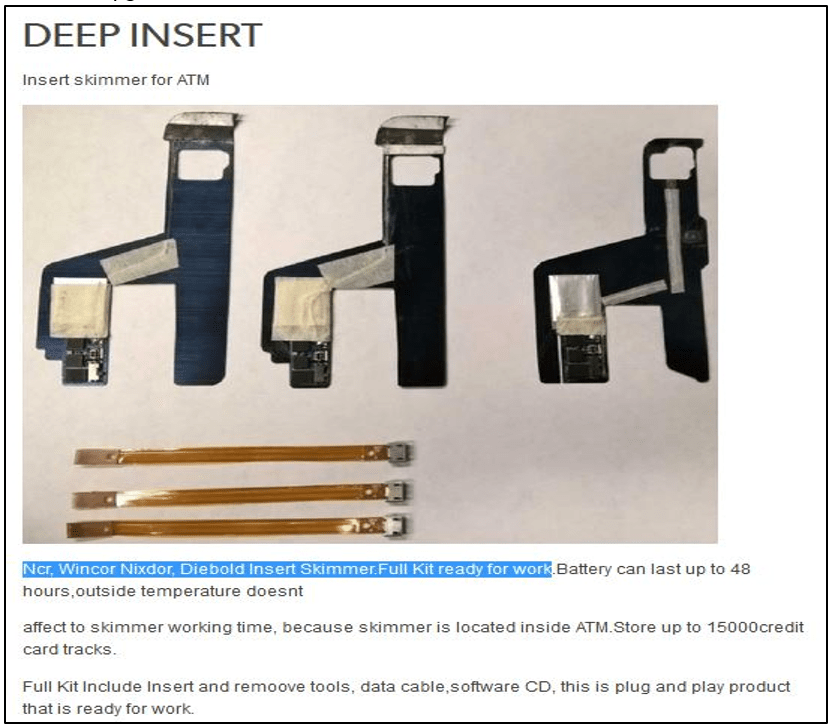
Method 3: ATM Hacking Appliances
There are a number of ATM Skimmer Shops on the dark web that offer various ATM Hacking Appliances such as EMV Skimmer, GSM Receiver, ATM Skimmer, POS, Gas Pump, Deep Insert, etc. Many shops offer a package of these different devices together.
These devices have a range of applications. On the one hand, there is a special category of Deep Insert devices which are attached to the ATM machines to extract sensitive financial information of the users. At the same time, there are certain packages where the attacker doesn’t have to be physically present at the ATM machine to install malware. Appliances such as Antenna allow hackers to carry out their attacks remotely, which makes it far more difficult to catch the perpetrators.
These shops are available on the dark web and keep getting updated with newer devices including Terminals, Upgraded Antenna, custom-made ATM Skimmers, RFID Reader/Writer, and so on.
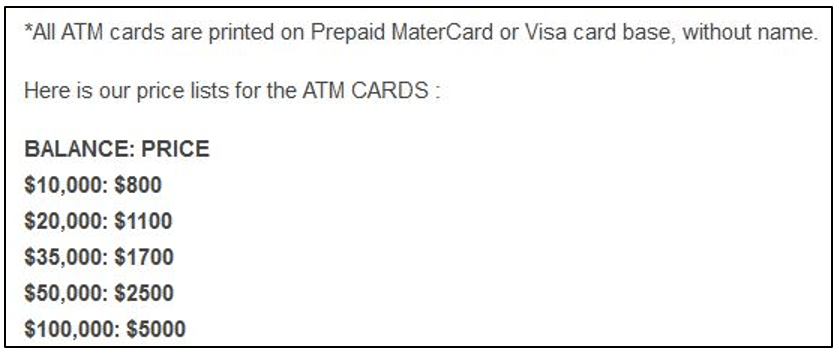
Method 4: Prepaid Cards
There are shopping sites on the dark web that offer both Bank Fullz and physical bank cards on their platform. While the Fullz cards are used for online transactions, physical cards can be used at ATMs. Some sites also offer prepaid credit credits, and the price of the card is obviously commensurate with the balance available on the card.
Method 5: Tutorials and Case Studies
There are a number of tutorials and real-world case studies available on forums on the Dark Web. For instance, there’s a detailed tutorial on an underground hacking forum that discusses how bank accounts can be compromised using Botnets. Many tutorials that contain detailed instructions on how to hack ATMs also come up for sale on different Dark Web shops, usually priced at $100 each.
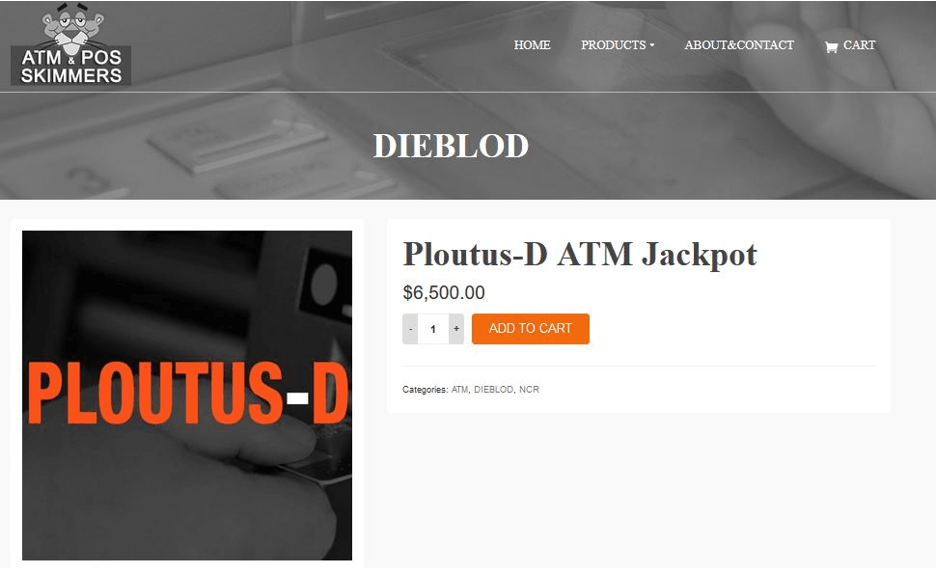
Method 6: Ploutus-D
The malware Ploutus-D has been used in recent ATM attacks. The malware compromises important components of a well-known multivendor ATM software and gains control of hardware devices like the cash dispenser, card reader, and pin pad. This means that any hacker can dispense all the cash in the machine in a matter of seconds. The source code of Ploutus-D along with detailed instructions are now being sold on various marketplaces on the dark web.
Summing Up
It’s hard to imagine that the cash machines that are a part of our everyday life can actually be this vulnerable to attack. Yet, as we’ve seen in the course of our work at CloudSek, ATM hacking is becoming more and more commonplace, especially with the availability of devices that allow hackers to access ATMs remotely. Since banks usually have the same configuration on a large number of ATMs, a single successful attack can usually be replicated on a much bigger scale.