SUMMARY
While Airtel denies the data breach, some of the leaked phone numbers have been confirmed to be of active Airtel subscribers
The leaked data included names, phone numbers, DOB, gender and Aadhaar numbers, among other sensitive user details
The hacker released the data last month after failing to get a ransom from Airtel
In an alleged data breach, sensitive information of 25 lakh Airtel users was made publicly available on a website. While Airtel has denied the data breach, some of the leaked phone numbers have been confirmed to be of active Airtel subscribers
The data was allegedly leaked by a hacking group named Red Rabbit and included names, phone numbers, dates of birth, home addresses, Aadhaar and international mobile subscriber identity (IMSI) numbers.
Notably, KYC requirements for Indian telcos make the collection of the above data from each user mandatory.
According to cybersecurity researcher Rajshekhar Rajaharia, who alerted Inc42 of this development, the hacker’s website, which contained the stolen data, went live sometime last month, after he had failed to get Airtel to pay a ransom for keeping news of the data breach under wraps.
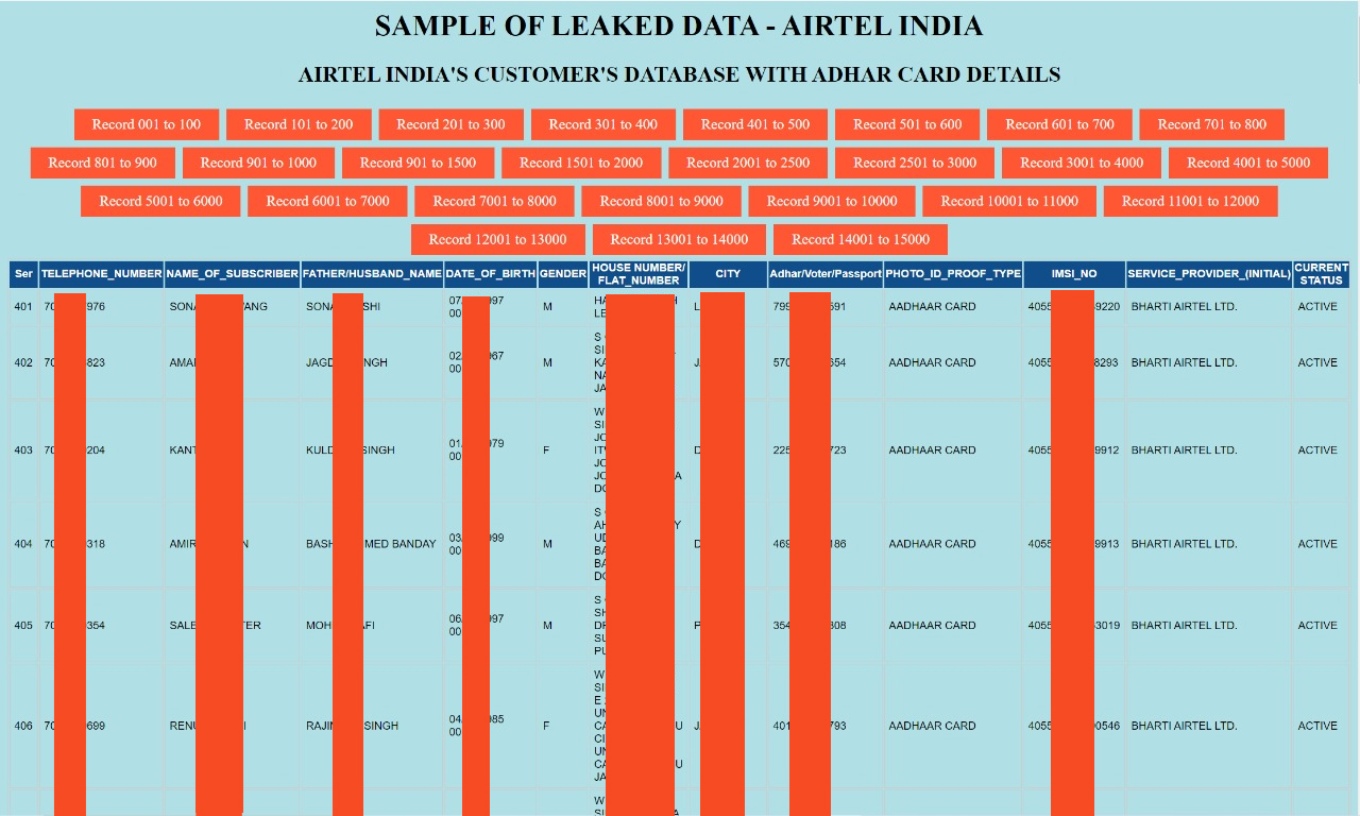
The hacker had claimed that the data of 25 lakh users was just a sample, and hence, all the affected users were from Jammu and Kashmir. The hacker claimed to have data of Airtel subscribers from several other Indian states and union territories and had threatened to make it public if the telco didn’t pay a ransom of around $3,500 worth in bitcoins. That ransom didn’t materialise and the hacker subsequently posted the sample data online, also mentioning that the fuller database was up for sale.
However, soon after Rajaharia shared information about the data leak on Twitter, the hacker’s website was pulled down. It is unclear if the website was pulled down voluntarily by the hacker or if it was the action of authorities.
According to Rajaharia, the hacker claimed to have stolen the data by uploading a shellcode onto the victim’s server. Shellcode is a set of instructions that executes a command in software to take control of or exploit a compromised machine.
Airtel Denies Data Breach Despite Video Proof
In a statement, Airtel denied any data breach.
“We confirm that there is no data breach at our end. In fact, the claims made by this group reveal glaring inaccuracies and a large proportion of the data records do not even belong to Airtel. We have already apprised the relevant authorities of the matter.”
Inc42 could confirm that at least some of the phone numbers in the leaked dataset belong to Airtel subscribers. We are also in possession of a proof of concept (PoC) video of the attack, which shows the hacker handpicking certain leaked phone numbers and verifying them to be Airtel subscribers through the telecom company’s SDR portal.

Another short video reveals the emails exchanged between the hacking group, Red Rabbit and Airtel’s security team, starting December 31, 2020. In the chat, while the hacker talked about finalising a deal, Airtel’s security team responded by saying that they had apprised their seniors about the development, also asking the hacker to take down the website before the company confirmed the next steps.
A source told us that the hacking group had been trying to finalise a deal with Airtel for $3,000 since October 2019. Moreover, initial attempts were made by the group by posing as a journalist from Delhi, then as a police official. The source added that Airtel didn’t give in to the demand for a ransom, since the company wasn’t convinced about the authenticity of the data which the hacker had purportedly stolen.
The source felt that the data could have been stolen from third parties, possibly even government agencies, with whom Airtel and other telcos are required to routinely share user data. However, cybersecurity expert and CEO of Netmonastery, a Mumbai-based network security company, Shomiron Das Gupta, talked about Airtel’s cybersecurity frailties.
“Airtel’s cyber vulnerability is not new. Earlier in 2019 too their data vulnerability was brought to the attention of the company,” recounted Das Gupta.
Airtel’s Dodgy Cybersecurity Track Record
In 2019, an independent security researcher had discovered a flaw in the Application Programming Interface (API) of Airtel’s mobile app, which could have exposed the data of 300 Mn users. Airtel had then claimed to have fixed the flaw immediately.
“The possibility of the hack into Airtel’s systems cannot be ruled out. The hacker could have breached the company’s server and created a back door entry,” he said.
It is worth mentioning that as per the Personal Data Protection Bill, 2019, set to be tabled in Parliament during the ongoing budget session, data fiduciaries are required to pay a penalty if they fail to comply with data processing obligations, directions issued by the Data Protection Authority, and cross-border data storage and transfer requirements.
The PDP bill mandates data fiduciaries — which collect, store and process users’ personal data for providing a service — to notify the DPA about a data breach that is likely to cause harm to customers, failing which, the fiduciary would have to pay a fine of up to INR 5 Cr or 2% of the worldwide turnover of the fiduciary, whichever is greater.
In October last year, observant Twitter users had flagged a passage in Airtel’s privacy policy, which said that the company and its authorised third parties could collect store and process the following types of sensitive personal information from their users: genetic data, biometric data, racial or ethnic origin, political opinion, religious and philosophical beliefs, trade union membership, data concerning health, data concerning natural person’s sex life or sexual orientation, password, financial information (details of Bank account, credit card, debit card, or other payment instrument details) and physiological information.
Airtel had later posted a clarification and updated its privacy policy.